Understanding Software Environments: Development, Testing, Staging, and Production
Purpose, Practices, and People Behind Each Stage of the Software Delivery Lifecycle

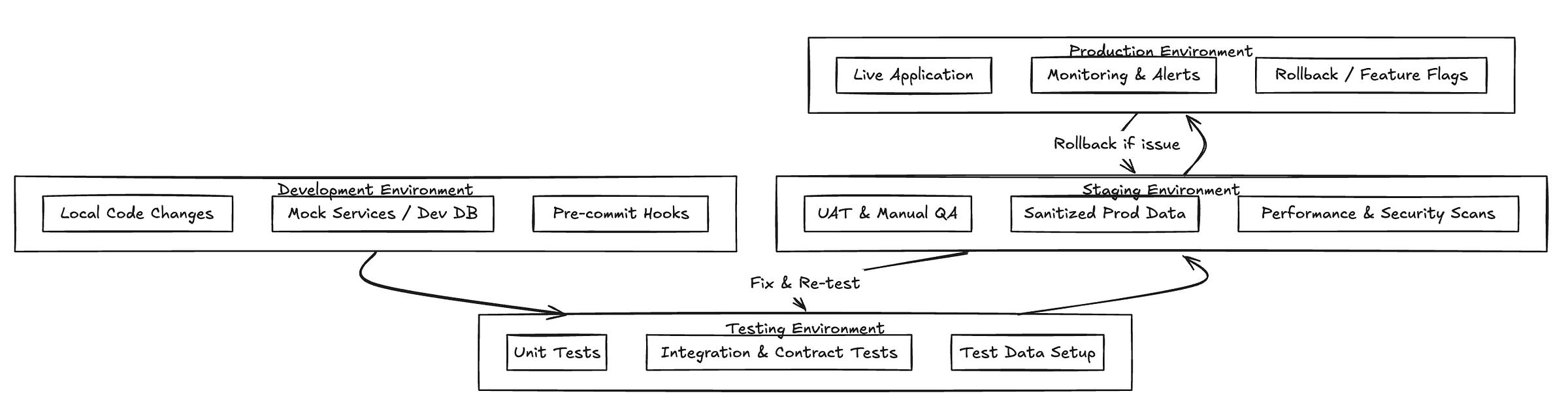
In modern software engineering, systems are rarely deployed directly from a developer’s machine into production. Instead, a series of isolated environments provide checkpoints where code can be built, validated, and approved before reaching end-users. This layered approach introduces consistency, safety, and predictability into the software delivery lifecycle.
Each environment — development, testing, staging, and production — has its own purpose, audience, and setup considerations. These environments are tightly integrated into the CI/CD pipeline and form the foundation of reliable engineering and DevOps practices.
From Development to Production Environments
Development Environment
The development environment is the first layer in the delivery chain. It is where developers write, run, and test their code locally or in a shared sandbox. This environment is designed for rapid iteration and debugging. It is usually loosely configured, allowing for mock services or local databases, and does not aim for production parity.
Its primary users are software engineers, who need freedom and speed to experiment and build features without impacting others. Occasionally, technical leads and code reviewers also interact with this environment to validate architecture decisions or design patterns.
A properly set-up development environment includes version-controlled configuration files, local build tooling, dependency management, and optionally a connection to remote services via mocks or stubs. Integrating linting, unit tests, and pre-commit hooks ensures quality is enforced from the first line of code.
Testing Environment
The testing environment is used to run automated tests — including unit, integration, contract, and regression tests — in a clean and reproducible setting. It is typically reset or recreated for every CI pipeline run to guarantee test isolation.
This environment simulates the application’s behavior under specific conditions and is designed to surface bugs early in the delivery lifecycle. Quality Assurance (QA) engineers, test automation developers, and CI maintainers are its core users.
This environment must include accurate test data, seeded databases, and full application stacks. Test coverage reports, execution logs, and performance metrics generated in this stage inform developers about the stability of their changes. It's important that the testing environment be as deterministic as possible — meaning every run should be consistent and reproducible.
Staging Environment
The staging environment is the closest replica of production. It runs the full application with production-grade configurations, real services, and often sanitized real data. The purpose of staging is to validate that code integrates well with the real-world setup and that deployments function as expected.
It's used to perform user acceptance testing, exploratory testing, performance benchmarking, and security scans. The stakeholders of this environment include QA, product managers (PMs), designers, and sometimes internal beta testers.
Because staging is a mirror of production, infrastructure parity is critical. The environment should use the same deployment methods, monitoring, alerting, and access controls. Best practices dictate that deployments to staging be gated by successful testing and peer review.
Production Environment
The production environment is the live system accessed by end users. It is the final destination of every release and must maintain high availability, performance, and security. Its users include customers, client applications, operations teams, and observability systems. Any failure in production is considered a critical event and should be mitigated with utmost urgency.
In production, infrastructure is managed with redundancy, scalability, and disaster recovery in mind. Logging, tracing, error monitoring, and anomaly detection are critical. Rollbacks, blue-green deployments, or canary releases should be built into the CI/CD pipeline to minimise risk.
Manual approval gates or scheduled releases are common, especially for critical applications. Access to production must be strictly controlled, and feature flags should be used to toggle functionality without needing new deployments.
Best Practices for Setting Up Environments in CI/CD
Creating environments that support stability and speed requires careful infrastructure planning and automation. Each environment should be defined using infrastructure-as-code to ensure repeatability. Configuration files (e.g., .env, Helm values, Terraform modules) should clearly separate concerns, allowing each environment to override only what’s necessary.
CI/CD pipelines must treat each environment as a stage. A good pipeline will first run unit and integration tests in isolated test environments, then promote builds through staging with acceptance and performance validations, and finally deploy to production only after approval or automated gating. Secrets management should vary by environment and never leak production credentials into testing or development stages.
Isolation between environments is critical — network rules, databases, and credentials must not overlap in ways that risk data leaks or contamination. Cleanup routines are equally important, especially for ephemeral or shared environments, to avoid stale states affecting test accuracy.
Conclusion
Treating environments as first-class citizens in the software lifecycle enables better quality, faster feedback, and safer releases. Each environment plays a distinct role: development fuels creativity, testing ensures correctness, staging validates reality, and production delivers value. By thoughtfully designing and automating these environments within CI/CD, engineering teams can move fast and deploy with confidence.